Cybersecurity and Risk Management Framework

Cybersecurity Defined
The official definition of cybersecurity is, ???Prevention of damage to, protection of, and restoration of computers, electronic communications systems, electronic communications services, wire communication, and electronic communication, including information contained therein, to ensure its availability, integrity, authentication, confidentiality, and nonrepudiation.??? ??? DoDI 8500.01
- Mission
- Prevent damage, protect, restore
- Cyber Items
- Computers, electronic communications and services, wire communications, electronic communication info
- To Ensure
- Confidentiality, integrity, availability (non-repudiation and authentication)
DoDI 5000.90 requires that program protection planning include cybersecurity. It also identifies two cybersecurity activities, Assess and Authorize, that are applicable within the Defense Acquisition System. DoDI 8500.01, Cybersecurity, defines cybersecurity and describes types of DoD information technology (IT). The DoD IT descriptions are used to determine the scope and applicability of the two cybersecurity activities identified by DoDI 5000.82. A Cybersecurity Strategy is required for all acquisitions of systems containing IT and is included as an appendix to the Program Protection Plan (PPP). The cybersecurity risk management framework for DoD systems, referred to as ???the RMF,??? is required for all acquisitions containing IT.
DoDI 8510.01, Risk Management Framework (RMF) for DoD Systems, details policies and procedures for implementing the RMF.
Foundational Pillars of Cybersecurity
Cybersecurity has five foundational pillars. The key triad is known as ???CIA??? ??? Confidentiality, Integrity, and Availability.
Confidentiality
Information is not disclosed to system entities (users, processes, devices) unless they have been authorized to access the information.
Integrity
The property whereby an entity has not been modified in an unauthorized manner.
Availability
Being accessible and usable upon demand by an authorized entity.
Non-Repudiation
Assurance that the sender of information is provided with proof of delivery and the recipient is provided with proof of the sender's identity, so neither can later deny having processed the information.
Authentication
Verifying the identity or other attributes claimed by or assumed of an entity (user, process, or device), or to verify the source and integrity of data.
The RMF
According to DoDI 8510.01, Technology (PIT) systems. Each step feeds into the program???s cybersecurity risk assessment that should occur throughout the acquisition lifecycle process. It should be noted that there is an organizational-level RMF step, Prepare, that precedes execution of the RMF at the system-level that sets organization-wide, organizationally-tailored risk management roles, risk management strategy, risk assessment, control baselines, cybersecurity framework (CSF) profiles, common controls, impact level prioritization, and continuous monitoring strategy.
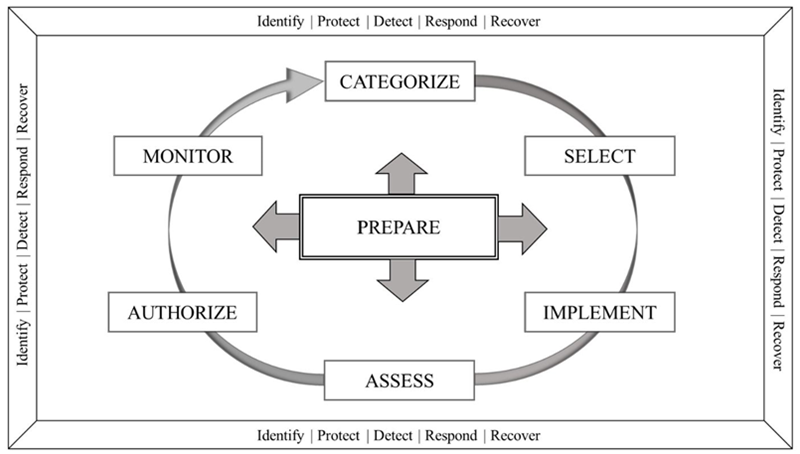
Step 1: Prepare
to execute the RMF from the system-level perspective by leveraging the organizational-level Prepare step to set the context and priorities for privacy and security risk management at the mission and business process and system level of the organization. At the system-level, this step includes:- Identifying the mission and business functions and processes that the system is intended to support
- Identifying the stakeholders that have an interest in the system
- Identifying and prioritizing the stakeholders??? assets
- Determining the system???s authorization boundary
- Identifying the types of information processed, stored, and transmitted by the system as well as the stages of their information life cycle
- Conducting or updating the system-level Mission-Based Cyber Risk Assessment
- Defining and prioritizing the system security and privacy requirements
- Placing the system within the enterprise architecture
- Allocating system security and privacy requirements to the system and to the environment that the system operates in
- Registering the system for the purposes of management, accountability, coordination, and oversight
Step 2: Categorize
the system in accordance with CNSSI No. 1253 based on the information analyzed, stored, and relayed by the system and an analysis of the impact of potential loss of confidentiality, integrity, and availability to organizational operations and assets, individuals, other organizations, and the Nation with respect to the loss of confidentiality, integrity, and availability of organizational systems. This step includes:- Documenting the system???s characteristics
- Conducting the system security categorization and documenting its results in the security, privacy, and supply chain risk management plans in a manner that is consistent with the enterprise architecture and the organization???s risk management strategy
Step 3: Select
an initial set of system security and privacy controls and tailor the controls as necessary to reduce risk to the system to an acceptable level based on a risk assessment. This step includes:- Selecting, baselining, tailoring, and allocating controls as required to protect the system commensurate with risk
- Controls are allocated to the specific system elements, i.e., machine, physical, or human elements
- Documenting the controls in the system???s security and privacy plans or equivalent documents, which are reviewed and approved by the Authorizing Official (AO)
- Developing a continuous monitoring strategy for the system that reflects the organizational risk management strategy
Step 4: Implement
the controls and describe how the controls are employed within the system and its operating environment. This step includes implementing and changing the controls in the system???s security and privacy plans as required, using applicable systems security and privacy engineering methodologies, and updating those plans as required to reflect the implementationStep 5: Assess
the controls to determine whether they are being correctly implemented, operating as intended, and producing the desired outcomes in meeting the requirements for security and privacy. This step includes:- Selecting an security control assessor (SCA) or assessment team with an appropriate level of independence to conduct control assessments
- Developing Security Assessment Plans (SAPs) and providing those plans to the SCA or assessment team in support of the conduct of test events, security, privacy, and supply chain risk assessments
- SAPs should be coordinated with developers and the developmental and operational testers and aligned with, and documented in, the T&E strategy
- SAPs are reviewed by the SCA and approved by the AO
- Conducting control assessments in accordance with the security and privacy assessment plans using automation, previous assessment results, and planned developer, engineering, developmental, and operational test events to the maximum extent possible
- Documenting assessment results, findings, and recommendations in system assessment reports (SARs)
- Taking remediation actions to address deficiencies in the controls implemented in the system and environment of operation and updating the related security and privacy plans for those actions
- Developing a plan of action and milestones (POA&M) detailing remediation plans for unacceptable risks identified in security and privacy assessment reports
Step 6: Authorize
the system based on a determination of whether the risk to organizational operations and assets, individuals, agencies, commands, and the Nation is acceptable, and cyberspace operational commanders??? requirements are met. Final risk determination and authorization decision definitions, e.g., interim authorization to test (IATT), authorization to operate (ATO), ATO with conditions, and denial ATO, and examples are on the RMF Knowledge Service (KS). This step includes:- Developing an authorization package, i.e., SAPs, SARs, POA&Ms, and the authorization decision document (RMF KS provides additional detail)
- A risk determination by the AO that reflects the risk management strategy
- Risk responses for determined risks
- An authorization decision for the system or the common controls is either approved or denied
- Reporting of authorization decisions, significant vulnerabilities, and risk to organizational officials
Step 7: Monitor
the system and associated controls on an ongoing basis in accordance with the continuous monitoring strategy, including monitoring the effectiveness of controls and ongoing testing, documenting system and operating environment changes, conducting control and risk assessments and impact analyses, and reporting on system security, privacy and supply chain risk management posture to the AO and other senior leaders and executives. This step also includes:- Updating risk management documents based on continuous monitoring activities
- Developing and implementing a system disposal strategy as needed
Cybersecurity RMF Conclusion
As noted above, there are specific documents that are required to support RMF decisions that are in addition to those required by program protection, e.g., Program Protection Plan, Cybersecurity Strategy, etc. However, the analysis supporting the RMF must be aligned to the analysis done by the system security engineer (SSE) and all the SSE specialists, e.g., software and hardware assurance, supply chain risk management, anti-tamper, defense exportability features, physical security, personnel security, etc., for technology and program protection.
Per DoDI 5000.02, cybersecurity applies to all six acquisition pathways of the Adaptive Acquisition Framework (AAF). According to DoDI 5000.90, cybersecurity activities should be initiated as early as possible and fully integrated into the DoD acquisition process, including requirements management, systems engineering, and test and evaluation.
As the integrating process for managing all security risks to a program, technology and program protection and cybersecurity must be aligned. The system security engineer leading program protection efforts must ensure that the security controls that are selected and implemented to fulfill the RMF requirements have a strong engineering basis and are implemented as part of the program's overall technology and program protection program.
For more information about cybersecurity for DoD systems, please consult the DAU Cybersecurity Training page.
References
Key Terms
- Adaptive Acquisition Framework Document Identification (AAFDID) tool
- Anti-Tamper (AT)
- Counterintelligence Support Plan (CISP)
- Cybersecurity
- Defense Exportability Features (DEF)
- Technology Targeting Risk Assessment (TTRA)
Policy and Guidance
- DoDD 5200.47E, Anti-Tamper (AT)
- DoDI 5000.82, Acquisition of Information Technology (IT)
- DoDI 5000.83, Technology and Program Protection to Maintain Technological Advantage
- DoDI 5000.90, Cybersecurity for Acquisition Decision Authorities and Program Managers
- DoDI 8500.01, Cybersecurity
- DoDI 8510.01, Risk Management Framework for Defense Systems
- CNSSI No. 1253 Security Categorization and Control Selection for National Security Systems
- Cyber Resilient Weapon Systems Body of Knowledge (CRWS-BoK) Tool
- DoD Program Protection Plan (PPP) Outline
- DoD Technology and Program Protection Guidebook
- NIST SP 800-18Guide for Developing Security Plans for Federal Information Systems
- NIST SP 800-30 Guide for Conducting Risk Assessments
- NIST SP 800-53 Rev. 5 Security and Privacy Controls for Information Systems and Organizations
- RMF Knowledge Service (KS)
DAU Training
- ACQ 160: Program Protection Planning Awareness, Lesson 5.3
- ENG 260: Program Protection for Practitioners
- CLE 074: Cybersecurity Throughout DoD Acquisition
- ISA 220: Risk Management Framework (RMF) for the Practitioner
- WSS 001, Cybersecurity and Acquisition Integration"
- WSS 003, Information System Security Manager (ISSM)
- WSS 004, Strengths, Weaknesses, Opportunities, and Risks
- WSS 005, Program Protection
- WSS 007, Cyber Table Top"
- WSS 008, Controlled Defense Information
- WSS 011, Cyber Training Range ??? Intermediate
- WSS 012, Defensive Cyber Operations (DCO)
- WSS 013, Cyber Training Range ??? Aviation Systemse
- DAU Cybersecurity Enterprise Team (CET) Training page
DAU Resources
On this page
- Cybersecurity Defined
- Foundational Pillars of Cybersecurity
- The RMF
- Step 1: Prepare
- Step 2: Categorize
- Step 3: Select
- Step 4: Implement
- Step 5: Assess
- Step 6: Authorize
- Step 7: Monitor
- Cybersecurity RMF Conclusion
- References
Related Topics
- Risk Management Overview
- Managing Cross Program Risks
- Critical Function/Component Risk Assessment
- Critical Program Information Risk Assessment
- Independent Technical Risk Assessment
- ESOH Risk Assessment